Identity theft continues to be more than just a costly headache. Once the bad guys have your identity information they can make repeated attempts to try to access your accounts, apply for credit in your name, and even steal your tax refund. This month we’re going to dig into some lesser-known, proactive steps you can take in the new year to protect yourself from becoming the target of identity fraud. And remember, If you suspect that your identity has been compromised, you have access to an Identity Theft Recovery Advocate as a benefit of your HomeFREE Checking account. These professionals are trained and ready to help you reverse the damage and get back on track quickly. Our experienced advocates know how to spot identity theft, and when necessary, will support you through the process of repairing any damages.
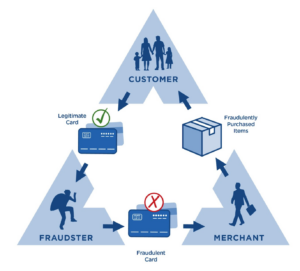
From the unknowing participant’s angle, triangulation fraud works like this: Bill Buyer sees a great deal on a laptop – it’s new and listed at 70% of the lowest price he has seen anywhere. Sara Seller is a relatively new vendor without many reviews, but nothing stands out as alarming on her seller’s profile. Bill Buyer orders the laptop, and not only does it ship quickly, he also receives a free wireless mouse with his shipment. Bill Buyer, obviously thrilled, leaves a positive review for Sara Seller, and purchases a discounted new printer she has listed as well. Two weeks later, after Bill has received the printer along with some free ink cartridges, he refers his friend Danny Discount to Sara’s page for more deals – only to find that Sara Seller’s eBay account has been deleted. Danny Discount, now curious, uses the wording of the laptop description to search for the same laptop that his friend Bill Buyer ordered. As luck (or deliberate design) would have it, he finds the exact same discounted item listed under a different auction account, which is really Sarah Seller’s alternate online seller identity, and the fraud cycle continues.
On the seller’s end, the fraud actually goes like this: Sara Seller has access to several stolen credit card numbers. She searches for trending electronics deals and finds the retail prices at the manufacturer’s website. Establishing a new online seller account and creating listings using stock images, she offers the electronics (not in her possession) at a great “Buy It Now” price. Bill Buyer, excited, orders a laptop, using a valid credit card. Sara Seller receives Bill’s money and uses a stolen credit card to order the laptop directly from the manufacturer, adding a wireless mouse to make a happier customer – it’s not her money, anyway. Sarah requests that the manufacturer ship the laptop and mouse to an “alternate address” which goes directly to Bill Buyer, now a very happy customer. The victim of this scam is, of course, the owner of the stolen credit card who is hopefully watching their card activity so they are alerted to these fraudulent transactions. As this crime is perpetrated using an existing credit card, there are no credit monitoring alerts. After a few similar transactions, each earning Sara Seller a few hundred dollars, she closes her eBay account and opens another one – to run the same scam again.
Sara has no shortage of stolen credit card numbers and nothing tracing her to the fraud, as her name and address are never involved. Bill Buyer is unknowingly used as a money mule, but he gets what he wants and more. We know that there is a loss to the person who owns the stolen credit card, and now he or she must go through the steps to dispute the fraudulent transaction with their bank, proving that it was not them that placed the order for the merchandise in question. If successful, this leads to a loss for the financial institution which must reimburse the stolen funds to the credit card. These fraud losses impact our economy to the tune of billions of dollars annually.
Another twist on this scam goes like this: After Bill Buyer makes his second purchase (the printer if you recall) from Sara Seller, Sara knows that she has Bill hooked. Sara contacts Bill to say that there was a processing glitch and there were actually three printers ordered under Bill’s eBay account. Sara is very apologetic and asks Bill to provide his credit card information so she can process the refund directly to his card without having to wait for the order to process through eBay. As her story goes, she wants to repay the money before the transactions hit his credit card. She offers to ship a free pair of earbuds for his trouble. Bill, not wanting his account to get hit for several hundred dollars more than he expected, provides the credit card information to Sara. Now the criminal has a new credit card to use for further fraud.
Watch this engaging video, entitled Confessions of an Nespresso Money Mule, about a woman who realized she was an unwitting part of a scam like this and what she tried to do about it.
Four things to watch out for when purchasing goods from an online auction site like eBay:
-
New seller accounts with little history and only recent feedback
-
Invalid contact information or strange email addresses
-
Items are shipped from a manufacturer’s address rather than the seller
-
Multiple similar items are listed at the same time on the seller’s account with generic pictures that could easily be found online
What should you do if you think you might have participated in triangulation fraud as an innocent money mule?
-
First, even though it seems obvious, stop purchasing from the seller. While it can be tempting to continue to benefit from discounted prices and free goods, remember that there are multiple victims in this scam: businesses, financial institutions, and individuals whose credit card numbers have been stolen and possibly even yourself, as you could go on a list as a willing target for other criminal scams.
-
Next, report the seller to the relevant online platform’s customer service or fraud department. They will look for suspicious patterns in the seller’s listing behavior and if found to be fraudulent, will act accordingly.
-
And third, report your concerns, in as much detail as possible, to the Federal Trade Commission at their website ftc.gov/complaint.
This is just one of several ways that individuals can fall victim to a money mule scam. Check out this article from the Federal Trade Commission on other types of Money Mule Scams to protect you and your family members. To summarize, never accept a job that requires you to transfer money, don’t accept a prize that requires any payment from you to collect it, and get out of any online relationship that involves sending money back and forth.
Remember, if something seems too good to be true, it probably is. And as always, if you fear that you have fallen victim to a scam that might have compromised your identity, you have access to an Identity Theft Recovery Advocate as a benefit of your HomeFREE Checking account. Our trained professionals are ready and available to support you through the process of getting back on track.



 The workers are sooo nice and friendly!!"
The workers are sooo nice and friendly!!"